# Webhooks and token authentication
You can safeguard trigger events that are triggered by third-party system calls by creating a token with an assigned user context. This check is based on the WebSub standard (opens new window). Third-party systems that do not implement this standard can be provided the token as a query parameter in the webhook URL.
# Token administration
The token administration area provides an overview of all endpoints and their respective tokens.
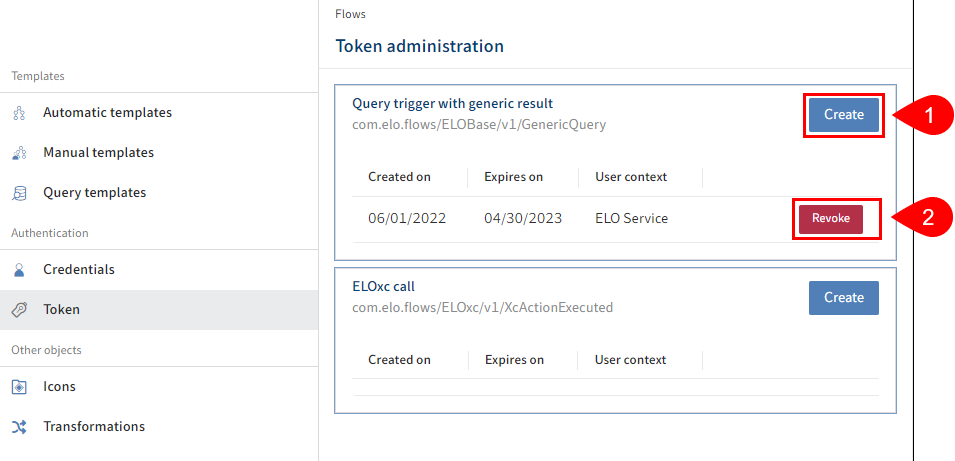
Selecting the Token entry in the sidebar opens the token administration area.
All the endpoints used and their tokens are listed in the token administration area. You can also create, change, and revoke tokens here.
The endpoint entries are collapsed to begin with for a better overview of the endpoints and their respective tokens. Only when you select an endpoint does the system show a list of the tokens for exactly this endpoint.
1 Create: Create a new token. You will find more under Token creation.
2 Edit: Double-click a token entry to open the editing dialog box. The user context and expiration date of the token can be changed there.
3 Revoke: Third-party systems that use this token are no longer authorized to trigger trigger events.
# Token creation
A token requires a user context and an expiration date. This can be configured in the settings dialog box.
- In the token administration area, select an endpoint.
The endpoint expands.
- In the endpoint, select Create.
The Token dialog box opens.
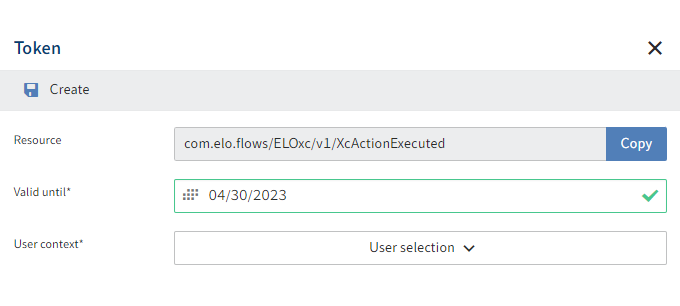
In the Valid until field, enter how long the token should be valid.
Select Select users.
A search field opens.
Search for the user you want the token to run through.
Information
The user must be created in the Credentials menu item.
Select a user.
Select Create.
ELO Flows creates a new token.
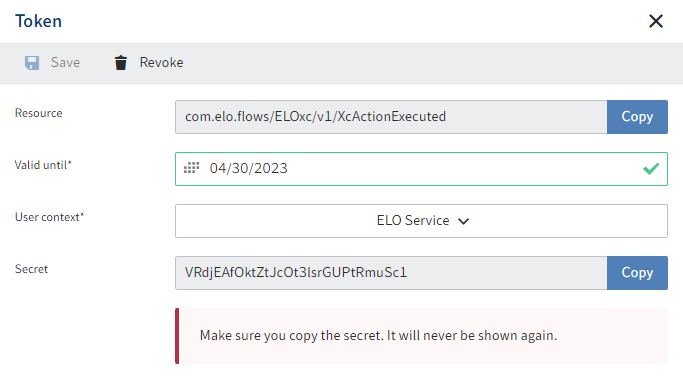
After creation, the secret used for webhook registration is shown in the dialog box.
Important
The secret cannot be viewed again. Create a copy for this reason.
# Query parameter
Not every third-party system supports the WebSub standard. To be able to use this kind of system anyway, you can provide a query parameter containing the token secret to the webhook URL. This URL is then used to register the webhook in the third-party system. As a result, the secret is provided from the third-party system when the trigger event is triggered for authentication.
A possible endpoint can look like this, for example:
http://<server>:<port>/ix-<repository>/plugin/de.elo.ix.plugin.proxy/
flows/api/v1/trigger/com.elo.flows/ELOBase/v1/ObjectCreated?token=07Cz3CCkYiW32OXrRuJZ0bFjyoupBQ
Please note
Query parameters should only be used in the event of a possible HTTPS connection.