# LDAP interface configuration
The LDAP interface configuration area in the ELO Administration Console is where you edit the connection settings, user import settings, and attribute assignment settings of the configuration file ldap.json. The file ldap.json is stored in the repository under the following path:
Administration//IndexServer Scripting Base//_ALL//ldap.json
Information
Path changes are possible in the following cases:
- If you want to make a special configuration for an ELO Indexserver, copy the file to the directory of the respective ELO Indexserver and make changes to the file there.
- If you'd like to make different configurations for different ELO Indexservers, you will need a separate file for each ELO Indexserver.
The configuration only applies to a single repository. If you edit the configuration in the ELO Administration Console, you need to restart the ELO Indexserver of the repository. If there are multiple ELO Indexservers, you need to restart all of them.
Please note
You should not use LDAP to authenticate the ELO Service account (or the service account used). This allows the server-side ELO applications to run independently of the LDAP configuration. Disabling the LDAP connection can cause the ELO applications to no longer start. In this case, you will not be able to enable the LDAP connection in the ELO Administration Console.
Administrator accounts should not be authenticated via LDAP either.
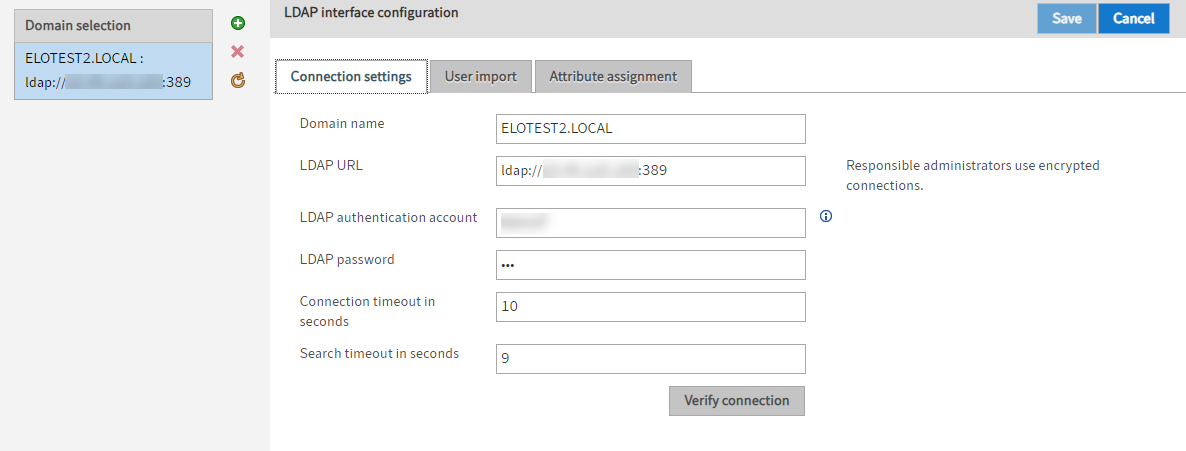
You can make settings for multiple domains.
Under Domain selection, you see a list of available domains.
Add (green plus icon): Add settings for a domain
Delete (red X icon): Delete the settings of a domain
Reload data from server (yellow circle arrow icon): Reload the Domain selection area
Information
In case of connection problems, the ELO Indexserver log file can be set to debug. This makes troubleshooting easier.
# Connection settings
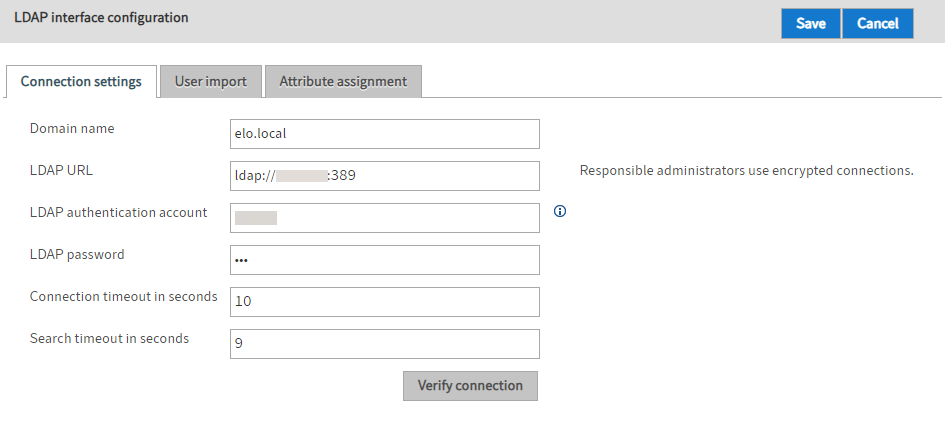
Domain name: Specify the DNS name or IP address of the domain here. The setting is used if the userPrincipalName is derived from the sAMAccountName.
Information
Only letters (without umlauts and special characters), numbers, periods, and underscores are allowed. The first character must not be an underscore.
LDAP URL The entries in the LDAP URL field determine the TCP connection to the LDAP server.
LDAP authentication account: SSO requires a technical account to search LDAP for the user name transferred by the SSO mechanism (usually sAMAccountName). Enter a userPrincipalName.
Please note
The account must have sufficient rights to read the user attributes and group memberships.
Please note
When using Kerberos: Disconnect the Kerberos account and the LDAP authentication account. The Kerberos account does not have to be created in ELO.
LDAP password: In the LDAP password field, you can enter the unencrypted password of the LDAP authentication account. The ELO Indexserver stores the password encrypted on restart.
Connection timeout in seconds: The LDAP interface terminates the connection to the LDAP server after this number of seconds. It then attempts to establish a connection with the next server in the list.
Search timeout in seconds: When searching for users or groups, this timeout value is passed to the LDAP server.
# User import
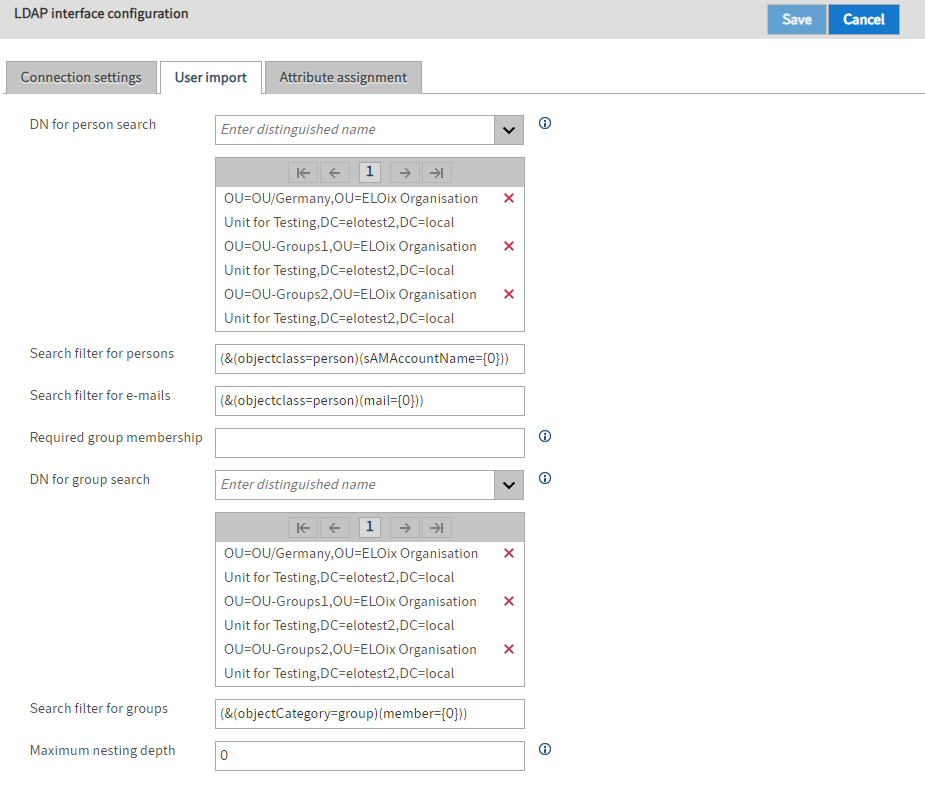
DN for person search: Use this field to specify which branches of the LDAP directory to search for users.
Please note
The list must not be empty.
Don't enter too many branches either. The more branches, the more imprecise the search.
Search filter for persons: You can use this filter to restrict the search for users.
Search filter for e-mails: The first time the user authenticates with an e-mail address, this filter is used to search for the user in the LDAP directory.
Required group membership: With this setting, you can use the common name to restrict authentication to users who are members of a certain group in the LDAP directory. This must be entered as the common name.
DN for group search: In this field, you specify which branches of the LDAP directory the groups that are eligible for synchronization must be in. If the list is empty, all groups of the user are included in group synchronization.
Search filter for groups: You can use this filter to restrict the search for groups of a user.
Maximum nesting depth: This field can be used to specify the depth of group nesting. This refers to the collection of user groups for group synchronization.
# Attribute assignment
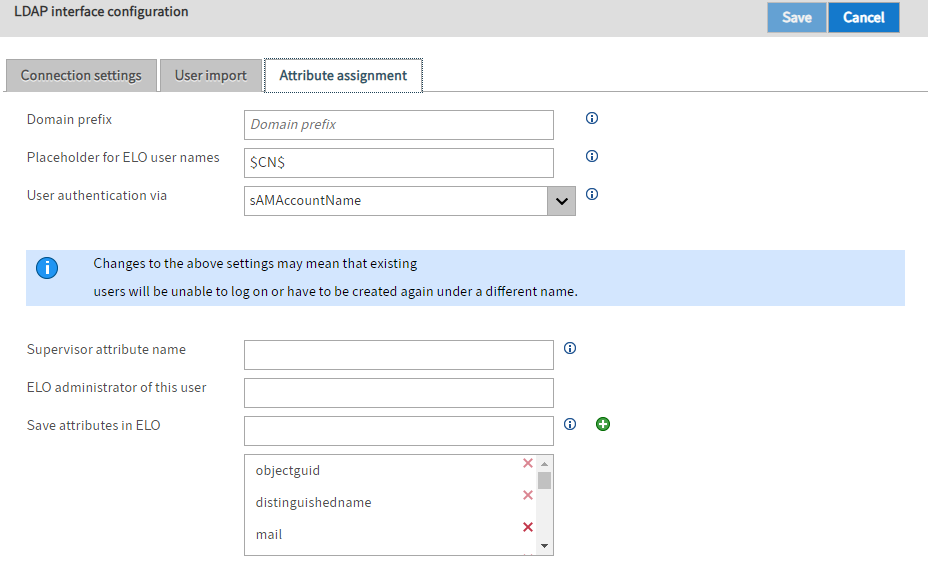
Domain prefix: The domain prefix is required if multiple domains are configured and the sAMAccountName is saved as the Windows attribute for the ELO user. There must be a separator at the end of the domain prefix. This separates the prefix from the user name. Ideally, you should use a backslash.
Information
If you are using SSO, the domain prefix must match the NetBIOS domain name.
You will find the corresponding domain prefix for SSO in the USERDOMAIN environment variable on the client computer. For SSO with domain prefix, you need to set the option "ntlm.domainUserFormat" in the ELO Indexserver config.xml file. If you set the option sAMAccountName in the User authentication via field and specify a domain prefix, the Windows user contains the account name with the domain prefix in front.
Information
For SSO authentication with NTLM, the option sAMAccountName must be selected in the User authentication via field.
Example:
sAMAccountName= fritzfrei- Domain prefix = ELO\
- Windows user = ELO\fritzfrei
Placeholder for ELO user names: The ELO user name can be made up of different LDAP user attributes. You can specify a format expression with placeholders. Enclose the placeholders in $ signs. They must also correspond to the LDAP attribute names.
User authentication via: In the drop-down menu User authentication via, you can specify whether you want to set the sAMAccountName, the userPrincipalName, or the UID as the Windows user attribute (see ELO user administration).
Please note
The setting selected in the User authentication via field must match the settings in the Search filter for persons field (User import tab). Pay attention to capitalization.
Any umlauts should also be identical between the Active Directory and ELO user names.
The ELO Administration Console checks LDAP for the following four attributes. The ELO Administration Console uses the first attribute set for the name.
LdapServerFactory.CONST.USERINFO.DISPLAY_NAME,
LdapServerFactory.CONST.USERINFO.CN,
LdapServerFactory.CONST.USERINFO.SAM_ACCOUNT_NAME
LdapServerFactory.CONST.USERINFO.DISTINGUISHED_NAME
Information
Some environments require a custom configuration. This field enables you to enter any values.
Supervisor attribute name: In this field, you specify which attribute is used to determine the supervisor of the ELO user. This is usually the attribute $manager$.
Please note
The supervisor must already exist in ELO.
ELO administrator of this user: In the field ELO administrator of this user, you can specify which ELO user to set as administrator for users created via the LDAP interface. You can enter the ID, GUID, or ELO user name.
Save attributes in ELO: In this field, you specify which attributes are to be transferred from LDAP to ELO.
To add an attribute, enter the name of the attribute in the field. Next, select Add (green plus icon).
To remove an attribute, select the X icon next to it in the list of attributes.
Information
Mandatory attributes cannot be deleted. In this case, the X icon is grayed out.