# LDAP import
With LDAP import, you can import users and groups from an Active Directory (AD) into the ELO system.
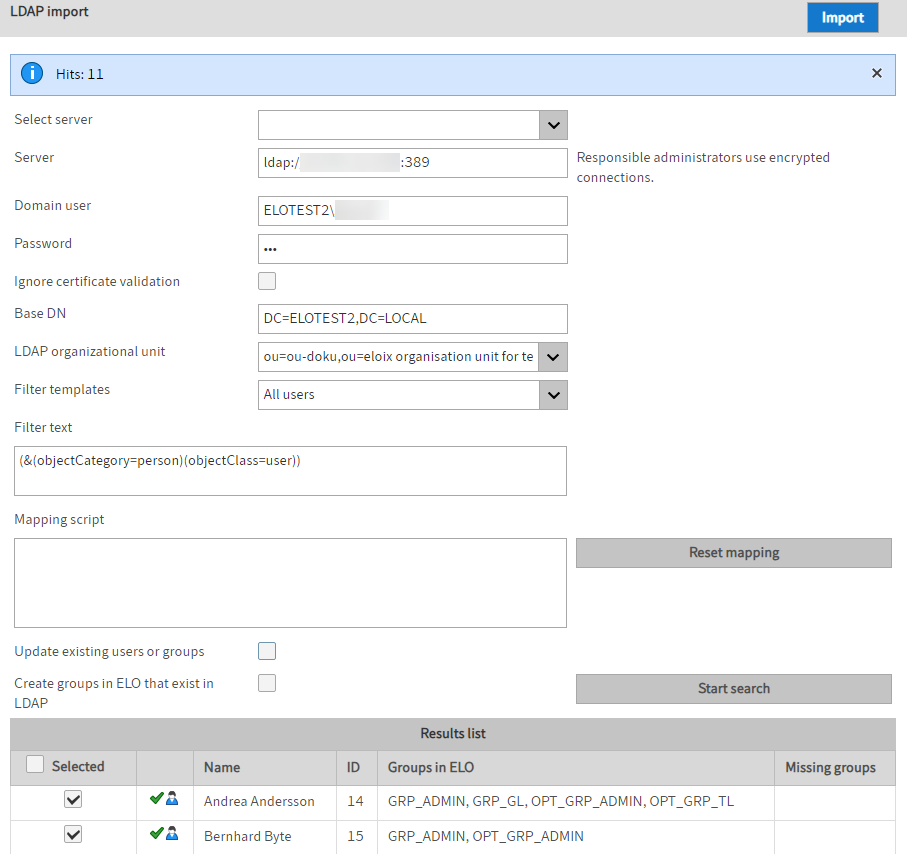
Select server: The ELO Administration Console attempts to find possible LDAP servers automatically. If this field is blank, no server will be found in the domain. This may be the case with a VPN connection, for instance.
Server: Enter the server for the LDAP connection here. You can also enter the IP address, port, or protocol here.
BNF: server ::=[ldap|ldaps]://[servername|IP address]:port
Please note
Use an encrypted connection, in this case LDAP via SSL (LDAPS).
Domain user and password: The authentication data consists of a name and password.
Ignore certificate validation: The certificate validation can be ignored if needed.
Base DN and LDAP organizational unit: These entries are used to select the correct branch of the LDAP directory.
Filter templates and filter text: Some LDAP filter expressions are already provided in the list and applied to the filter text so that they can be edited.
Mapping script: This setting allows you to edit the data as JavaScript code.
For more information, see the next section The mapping script.
Reset mapping: Deletes the text from the mapping script field.
Update existing users or groups: If the name can be resolved to an existing entry, this entry is only processed again if this setting is enabled.
Please note
LDAP groups are only read and used when users log on.
Create groups in ELO that exist in LDAP: Creates groups that do not yet exist in ELO.
Start search: Performs a search and shows the results.
Results list: Shows the list of the entries that will be imported. All valid entries are also selected. If invalid data is detected during the check, they will not be selected, and a note about the problem is shown in a tooltip.
# The mapping script
Default LDAP attributes are automatically mapped to ELO attributes. To allow more flexible customization, JavaScript code can be entered in the input field. It is embedded in a code frame and is executed for every data set in the LDAP search.
The ELO Indexserver has a data structure for the users and groups: the UserInfo object. This is described in detail in the ELO Indexserver technical documentation. It can be accessed in the mapping script using the variable name elo.
# Default mapping
- elo.type
- Based on the LDAP
ObjectClass=person - If the class exists, a user is created; otherwise a group is created.
- Based on the LDAP
- elo.name
- Based on the LDAP attributes
displayName,cn,sAMAccountName, anddistinguishedName. - The first LDAP attribute found is used as the name.
- Based on the LDAP attributes
elo.userProps[UserInfoC.PROP_NAME_OS]- The value of the
sAMAccountNameLDAP attribute is applied.
- The value of the
elo.userProps[UserInfoC.PROP_NAME_EMAIL]- The value of the LDAP attribute
mailis applied.
- The value of the LDAP attribute
elo.superiorId- The LDAP attribute
manageris evaluated.
- The LDAP attribute
- If the
managerattribute refers to an existing ELO user, the ID of this user is applied as the supervisor. elo.id- If the name refers to a valid ELO user, this ID is applied as the user ID. Otherwise -1 creates a new user.
# JavaScript code frame
At the debug log level, the generated script is output to the log file.
// rhino compatible modus on java 8 (nashorn)
load('nashorn:mozilla_compat.js')
// editable basic javascript mapping function Version 1.0
importPackage(Packages.de.elo.ix.client)
importClass(Packages.de.elo.ldap.LdapImportException)
function extractDN(v){
try{
var vv=v.substring(3,v.indexOf('=', 3))
return vv.substring(0,vv.lastIndexOf(','))
}
catch(e){}
}
function map(ixc, elo, ldap, userNames){
%% The text from the interface for the mapping script field is output here. %%
}
If the ELO Administration Console is started using Java 8, the Rhino compatibility mode is included.
public interface LdapImportMapping {
public void map( de.elo.ix.client.IXConnection ixc, de.elo.ix.client.UserInfo userInfo,
javax.naming.directory.Attributes attributes,
Map<String, de.elo.ix.client.UserName> userNames );
}
The JavaScript frame is accessed via the LdapImportMapping Java interface. In the map, the ELO name in lowercase is used as the key to the UserName object.
# Examples
- A data set can be excluded by setting elo.id=0.
if (elo.name.startsWith('_')){
elo.id=0
}
- Since JavaScript code can be used, it is also possible to view outputs for testing using the error reporting mechanism.
throw ldap.get('mail').getClass()
or also
throw userNames['administrator'].id
- A short example shows how to exclude items while checking the
mailattribute and set the display name for the remaining users.
var emailRegex = /^[\w._-]+[+]?[\w._-]+@[\w.-]+\.[a-zA-Z]{2,6}$/
var lMail = ldap.get('mail')
if (lMail){
lMail = lMail.get()
if(emailRegex.test(lMail)){
elo.name += ' ('+lMail.split('@').pop()+')'
// valid e-mail -> customize the display name.
}
}else{
elo.id=0
// invalid e-mail -> exclude
}